- SS&C Blue Prism Community
- Get Help
- Digital Exchange
- Issues Implementing MS Graph Outlook VBO
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Issues Implementing MS Graph Outlook VBO
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
22-02-23 03:38 PM
We are attempting to implement the Microsoft Graph API for accessing a shared Outlook mailbox. Currently, I am attempting to use the List Messages action, and am getting the following error message (have tested other actions with a similar error): {"error":{"code":"InvalidAuthenticationToken","message":"Access token is empty.","innerError":{"date":"2023-02-22T15:07:56","request-id":"xxx","client-request-id":"xxx"}}}
However, we've confirmed that the authentication token is still active. We have the following API permissions set:
Mail.ReadWrite (Delegated)
Mail.ReadWrite.Shared (Delegated)
Mail.Send (Delegated)
Mail.Send.Shared (Delegated)
For the inputs, we're using the shared mailbox (full email address) as the mailbox ID.
Thank you in advance for any help you can provide.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
22-02-23 09:34 PM
This is likely because you have an older version of the Utility - HTTP VBO deployed in your environment. I'd suggest grabbing the latest version from the Digital Exchange and try again.
https://digitalexchange.blueprism.com/dx/entry/3439/solution/utility---http
Cheers,
Eric
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
23-02-23 01:09 PM
Thanks @ewilson
We're now getting a 403 (Forbidden) error; any recommendations on what might be causing that? Have you seen any limitations with others around configs/access for shared mailboxes using the VBO?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
23-02-23 04:37 PM
Are you using an Application Access token or a Delegated Access token? Have you verified that the Client ID you have has to proper mail permissions in Azure AD? For mail this would include either Mail.Read.Shared or Mail.ReadWrite.Shared for reading from the shared mailbox. You would also need Mail.Send.Shared if you intend to send email from the shared mailbox.
Here's a link to the Microsoft Graph permissions reference:
https://learn.microsoft.com/en-us/graph/permissions-reference#mail-permissions
Cheers,
Eric
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
23-02-23 04:48 PM
We're using a Delegated Access token and do have the Mail.ReadWrite.Shared and Mail.Send.Shared permissions configured.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
23-02-23 05:16 PM
Ok, so the digital worker is essentially working on behalf of someone as a delegate. Have you verified that the user account, to whom the digital worker is working on behalf of, has permissions on the shared mailbox?
Cheers,
Eric
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
23-02-23 05:21 PM
Yes, we've confirmed that the account has permissions to the shared mailbox. Thank you for your continued help with this - I appreciate it!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
23-02-23 05:32 PM
Any chance the issue could be in the Manifest configurations? Would you be able to provide an example of what those should look like?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
23-02-23 08:59 PM
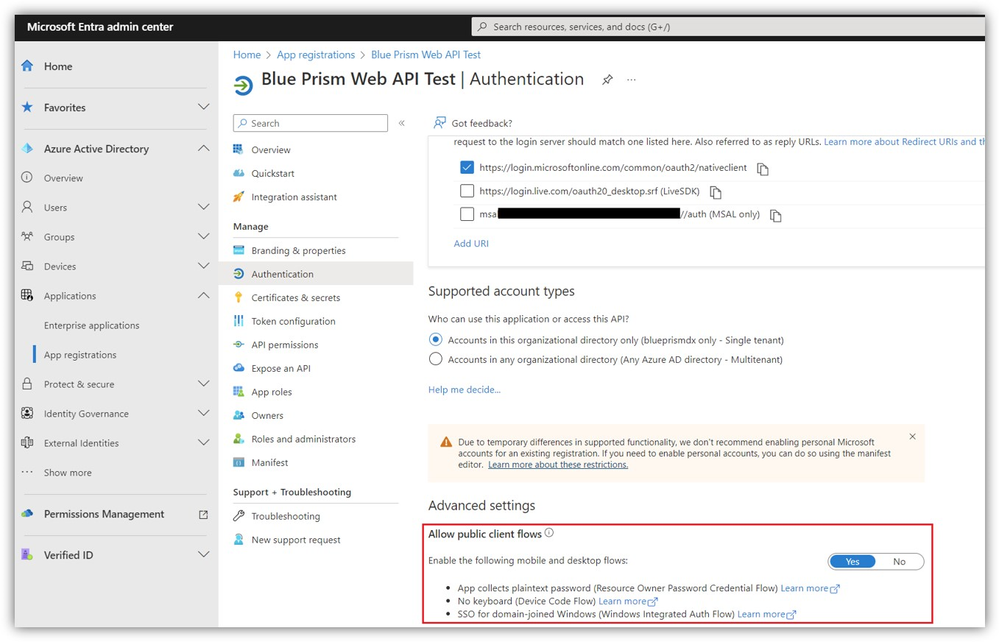
If you're trying to get a Delegated Access token you must pass in the Tenant ID, Client ID, Username, and Password. Do not pass in Client Secret because that automatically results in trying to get an Application Access token. The Username and Password are for the account your Digital Worker is trying to work on-behalf of. Also, I believe Delegated Access will require that you enable the Allow public client flows option within the Application Registration page for the Client ID you're using.
Here's an example of what that looks like in the Azure Admin page:
Cheers,
Eric
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
27-02-23 02:21 PM
Thanks, @ewilson . Ultimately, we decided to change configurations to Application level access with a Scope configured in the app registration to limit access to just the mailboxes needed. So far, everything seems to be working great now! Thank you so much for your help with this.
- MS Outlook Email VBO-Move Item Action Input Issue in Digital Exchange
- Outlook Graph API VBO- issue when mail is attached in Product Forum
- Outlook Graph API VBO- Delivery receipt issue in Product Forum
- RPC Server Unavailable Error with Microsoft Outlook Email VBO v10.4.1 in Product Forum
- Outlook issue while save attachment. in Product Forum