- SS&C Blue Prism Community
- Get Help
- Digital Exchange
- Re: Microsoft Graph/MSAL.net - delegated -device
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Microsoft Graph/MSAL.net - delegated -device
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
13-03-23 07:46 PM
Hi, I read many threads about Microsoft Graph and MSAL.net, but I didn't find my problem.
I am trying to authenticate to azure with delegated permission but am getting these errors.
When I run Microsoft Graph - Authentication::Get Delegated Access Token (Blue Prism VBO), the response was:
"invalid_grant","error_description":"AADSTS53003: Access has been blocked by Conditional Access policies. The access policy does not allow token issuance.
When I run MSAL.NET::Get Auth Token - Username and Password (Blue Prism VBO), the response was:
System.AggregateException: Se han producido uno o varios errores. ---> Microsoft.Identity.Client.MsalUiRequiredException: AADSTS50079: Due to a configuration change made by your administrator, or because you moved to a new location, you must enroll in multi-factor authentication to access.
In the Azure logs we found that the device information was empty and Microsoft support informed us that we must add it in the code.
The device is already hybridized in azure. The user account too.
So we need to add the device data to the action, any idea how to do it?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
15-03-23 03:44 PM
Hello @acatalano
My guess is that both of your errors relate to the fact that 2-factor authentication is enabled in your environment. There are two options here:
- Ask you IT folks to disable 2FA for any accounts used by Digital Workers.
- If that's not an option, there are a couple 2FA solutions available on the the Digital Exchange. I don't think either one has been tested specifically with authentication in Graph, but they may work for you.
Cheers,
Eric
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
15-03-23 05:55 PM
Hi @ewilson
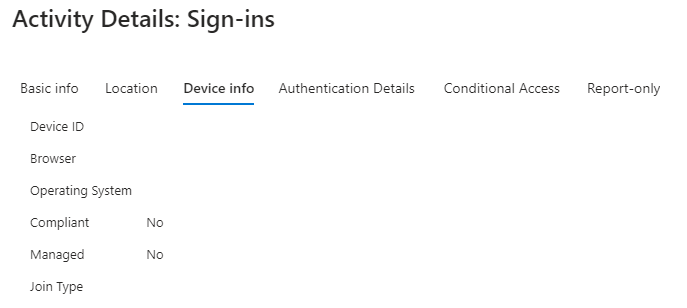
The IT team that manages Azure told us that the problem is that the information device was empty in our call and we need to add it. The user was already excluded from MFA.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
15-03-23 10:25 PM
I assume the MFA exclusion was made after your tests, otherwise you never should have received an MFA error. Regarding the device info, can your IT folks expand on what exactly they expect to see? Is it just the Azure AD joined device ID?
Cheers,
Eric
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
16-03-23 02:54 AM
@ewilson we did test every day, including after MFA exclusion.
Yes, because one of the security policies is to report the device ID. And as you will have seen in the image that I shared with you previously, it arrives empty.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
17-03-23 05:47 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
17-03-23 08:26 PM
@kkazantsev Yes, we tried and we received the token ok, the problem with that comes later because due to security policies they cannot give us permission to the apis. We must use delegate to control access.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
16-05-23 10:07 AM
Hello.
I have same issue as Agustin, we are currently searching for secure solution around this problem... And currently no clear answer that would be best in our situation.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
14-03-24 02:11 PM
@MantasPadimansk Did you solve that problem?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
17-07-24 09:47 AM
Hi,
Any solution to the issue, I am also using Delegated access, can't use application permissions due to policies, I am able to get the access token using client secret, but it is failing while sending mail: "Error: Access Denied", and when using username password to get the access token it is failing in getting it: Error:"The user or administrator has not consented to use the application with ID:".
- Unable to Authenticate Graph API in Digital Exchange
- MFA error while using Microsoft Graph Authentication VBO in Digital Exchange
- Error while getting the access token using microsoft365- outlook(Graph API) in Digital Exchange
- App Service Access Management for SharePoint CRUD - MS Graph API in Product Forum
- How to read outlook email from blue prism graph api - outlook email in Product Forum

