Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- SS&C Blue Prism Community
- Product News & Updates
- Product Ideas
- The security risk in a Credential manager - Passwo...
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Email to a Friend
- Printer Friendly Page
- Report Inappropriate Content
NagarjunaAtukur
Level 4
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Email to a Friend
- Printer Friendly Page
- Report Inappropriate Content
12-02-21
07:39 AM
Status:
New
After fetching credential values from credential manager, a developer can easily view the password by using simple calculate stage.
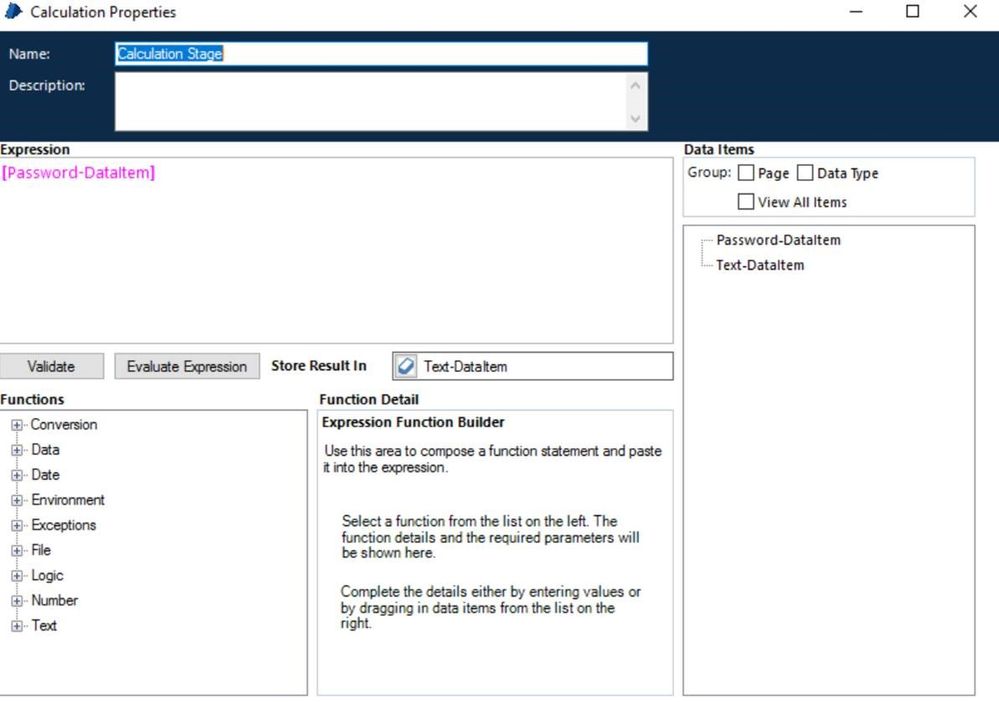
We are giving access to developers to utilize them for their automation process design. If a developer really want to view the password, he/she can easily view it with this loophole.
BP tool should prevent casting from password-type data items to text-type data items.
Thanks,
Nagarjuna A

We are giving access to developers to utilize them for their automation process design. If a developer really want to view the password, he/she can easily view it with this loophole.
BP tool should prevent casting from password-type data items to text-type data items.
Thanks,
Nagarjuna A
3 Comments
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Recently Completed Ideas
Idea Statuses
- New 896
- Needs More Info 65
- Reviewed 251
- Under Consideration 143
- Not Planned 198
- Planned 45
- Planned - Later 23
- Planned - Next 5
- Planned - Now 10
- Delivered 223
