- SS&C Blue Prism Community
- Get Help
- Digital Exchange
- MS Graph API - Authentication connector via MSAL
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
MS Graph API - Authentication connector via MSAL
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
07-09-22 02:31 PM
The MS Graph API - Authentication connector calls the https:// login.microsoftonline.com/* endpoint directly passing the username / password provided which is hitting Azure AD and attempting to authenticate directly against the cloud.
Because our company does not have password hash sync enabled this will not work as the account password is not stored in Azure AD.
Is there a solution possible using one of the available MSAL library's https://aka.ms/msal which will then allow for the authentication request to be redirected back to our on-premises hybrid identity infrastructure?
-----------------
Willy Vanroy
AXA Bank
-----------------
------------------------------
Willy Vanroy
Developer
AXA Bank
Europe/Brussels
------------------------------
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
07-09-22 10:07 PM
Have you checked the MSAL.NET connector?
Cheers,
------------------------------
Eric Wilson
Director, Integrations and Enablement
Blue Prism Digital Exchange
------------------------------
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
08-09-22 10:36 AM
It seems there is only support for Application Permissions, thus signing in with a Client Secret,
But with this type of deployment AXA cannot control from where the traffic is coming, also the document doesn't share the API permissions for which need to be assign so they cannot until they know guarantee that the permissions will fall within the range that is 'scopeable' (not sure that's a word) …
Is there a version which uses the MSAL.NET library but provides support for Delegated Permissions please? Possibly using the ROPC credential flow …
------------------------------
Willy Vanroy
Developer
AXA Bank
Europe/Brussels
------------------------------
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
08-09-22 12:41 PM
The permissions/scope are up to you. They are set on the application registration within Azure AD. For example, if I want to register an application that can work with email, I would add some subset of the various Mail permissions.
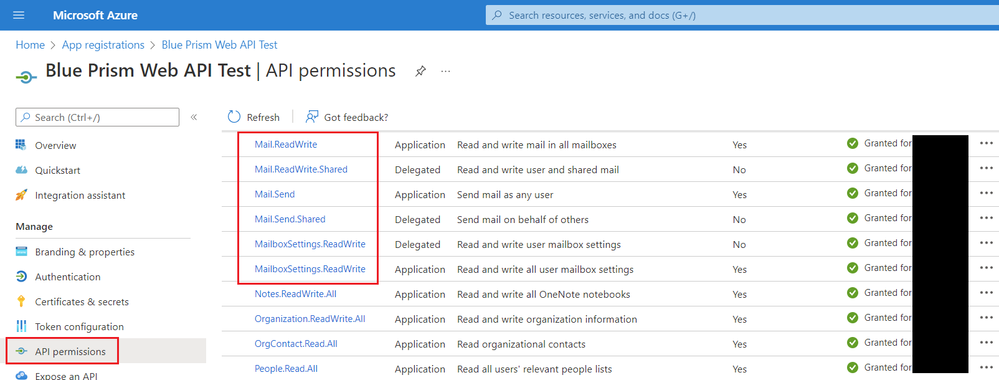
According to this link, Microsoft specifically recommends not using the ROPC flow:

Perhaps you can provide some more detail about how authentication works in your environment?
Cheers,
------------------------------
Eric Wilson
Director, Integrations and Enablement
Blue Prism Digital Exchange
------------------------------
- Excel Graph API - Issue in Get worksheet Name and Hide worksheet Action in Product Forum
- Microsoft Dataverse VBO Connectivity Issue in Digital Exchange
- Unable to Authenticate Graph API in Digital Exchange
- MFA error while using Microsoft Graph Authentication VBO in Digital Exchange
- Attaching files to an list item in SharePoint using API in Product Forum

