Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- SS&C Blue Prism Community
- Get Help
- Digital Exchange
- Gmail API vbo throws exception - invalid base 64 c...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
17-03-22 10:30 AM
Hello Community,
I am trying to get mails from Gmail through an API connector which is there in digital exchange, I have created the project in google cloud platform, enabled the Gmail API, created O-Auth credentials and service account as pre-requisites.
I have imported the Gmail API VBO and set the key in the credential manager, I am getting this error when I execute the process
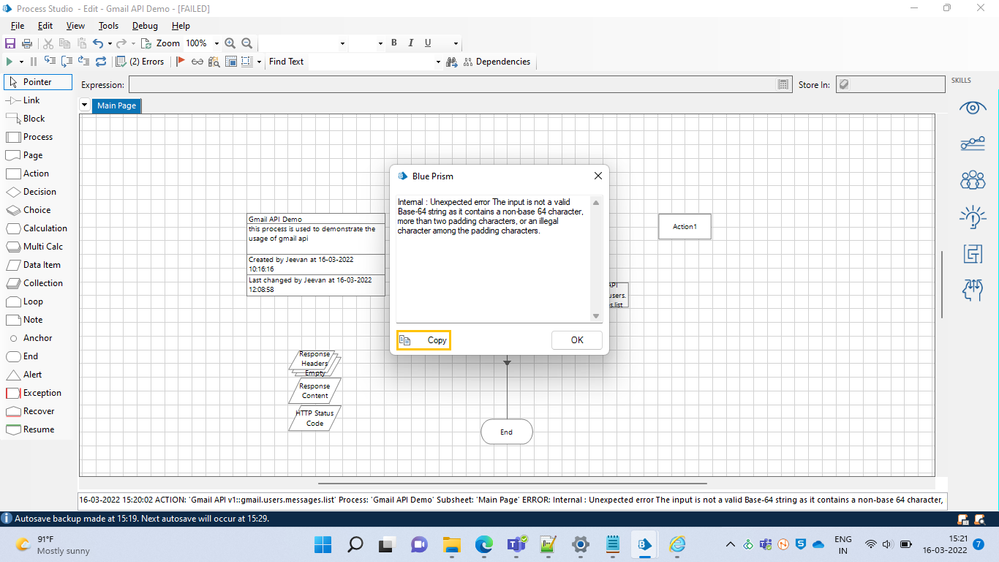
"Internal : Unexpected error The input is not a valid Base-64 string as it contains a non-base 64 character, more than two padding characters, or an illegal character among the padding characters. "
I request your help on resolving this, I have attached the screenshot below,
Please let me know if you require any more information.
Regards,
Jeevan
------------------------------
Jeevan R
------------------------------
------------------------------
Jeevan R
------------------------------
I am trying to get mails from Gmail through an API connector which is there in digital exchange, I have created the project in google cloud platform, enabled the Gmail API, created O-Auth credentials and service account as pre-requisites.
I have imported the Gmail API VBO and set the key in the credential manager, I am getting this error when I execute the process
"Internal : Unexpected error The input is not a valid Base-64 string as it contains a non-base 64 character, more than two padding characters, or an illegal character among the padding characters. "
I request your help on resolving this, I have attached the screenshot below,
Please let me know if you require any more information.
Regards,
Jeevan

------------------------------
Jeevan R
------------------------------
------------------------------
Jeevan R
------------------------------
Jeevan Rangaraju - AD01 Certified RPA Professional
Associate Consultant
Ernst & Young LLP
Bangalore, India
Email - jjeevan152@gmail.com
Answered! Go to Answer.
10 REPLIES 10
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
24-03-22 10:54 AM
@Jeevan R,
Is that your actual private key value? If so, it's invalid. That' way to short for a Google private key. To answer your question though, the way I typically handle the credential is by making use of Credential Manager. Here's an example:
Regarding your private key value, all you have to do is pull that out of the JSON-encoded credential file that Google makes available when you create the credential in the Google Console.
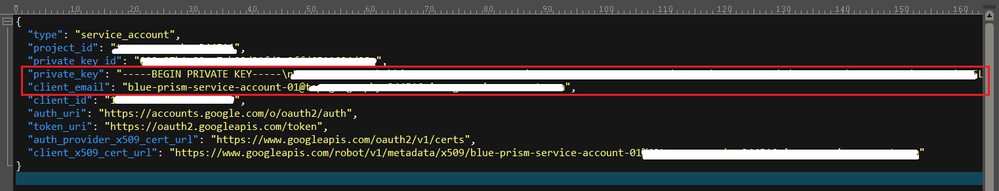
My private key value, from the first "-" to the trailing "\n" is 1732 characters long. You take those two values (client_email and private_key) and use them to populate your Blue Prism Credential Manager entry.
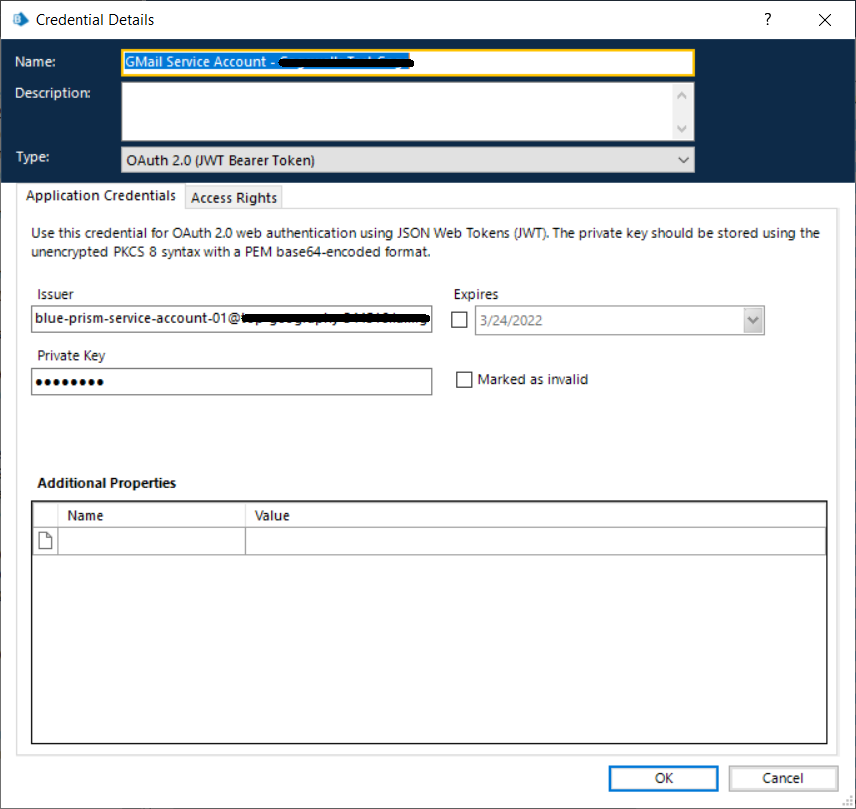
After I have the client_email and private_key values, I create a JWT Bearer token definition in Credential Manager. In reality, you could create a regular General credential if you wanted to now that the authentication will be handled by the new VBO. You just need a Username and Password value.
Next, in my process, I'll use the native Credential VBO to get the Username and Password value based on the name of the credential.
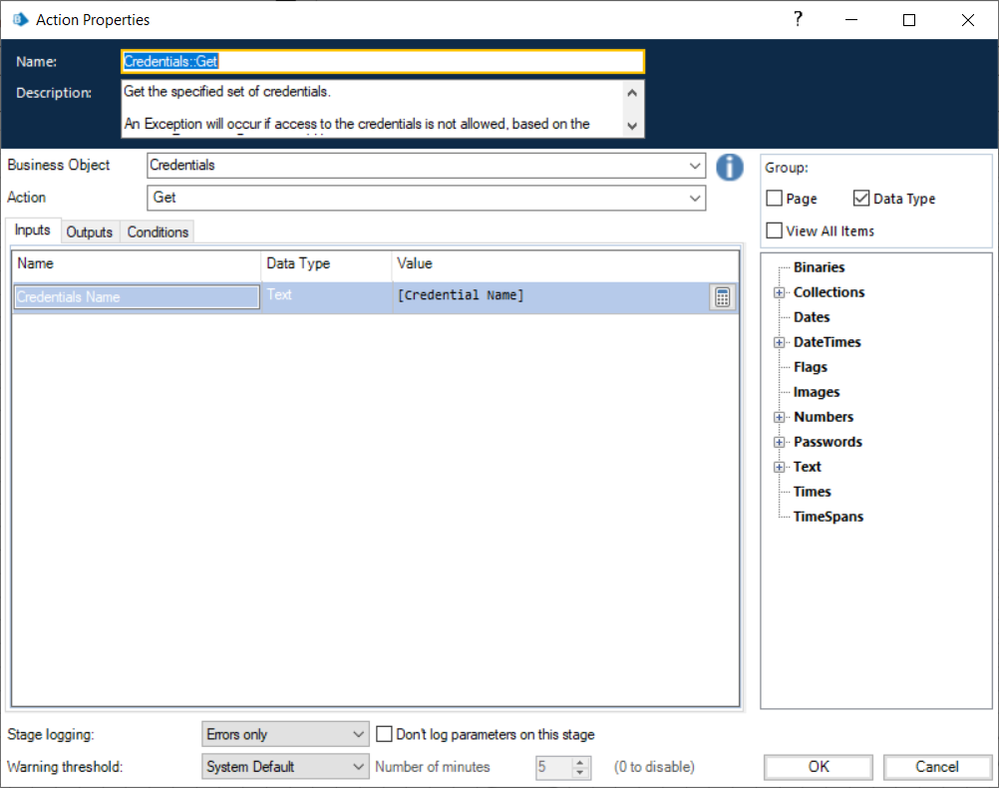
After that, I call the Google Cloud - Authentication VBO's Get Service Account Token action and pass in the Username, Password, my scopes, and the delegated user email address.
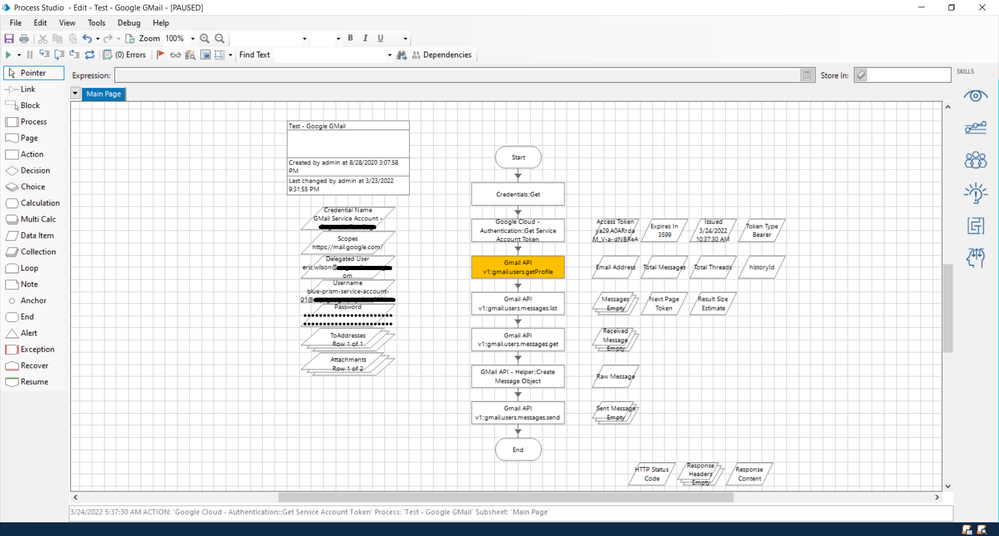
From that, I should receive a valid access token. The access token should be about 208'ish characters long. Hint: If the token is longer, and contains a bunch of periods at the end, it's not a valid token.
Cheers,
------------------------------
Eric Wilson
Director, Integrations and Enablement
Blue Prism Digital Exchange
------------------------------
Is that your actual private key value? If so, it's invalid. That' way to short for a Google private key. To answer your question though, the way I typically handle the credential is by making use of Credential Manager. Here's an example:
Regarding your private key value, all you have to do is pull that out of the JSON-encoded credential file that Google makes available when you create the credential in the Google Console.

My private key value, from the first "-" to the trailing "\n" is 1732 characters long. You take those two values (client_email and private_key) and use them to populate your Blue Prism Credential Manager entry.
After I have the client_email and private_key values, I create a JWT Bearer token definition in Credential Manager. In reality, you could create a regular General credential if you wanted to now that the authentication will be handled by the new VBO. You just need a Username and Password value.

Next, in my process, I'll use the native Credential VBO to get the Username and Password value based on the name of the credential.

After that, I call the Google Cloud - Authentication VBO's Get Service Account Token action and pass in the Username, Password, my scopes, and the delegated user email address.

From that, I should receive a valid access token. The access token should be about 208'ish characters long. Hint: If the token is longer, and contains a bunch of periods at the end, it's not a valid token.
Cheers,
------------------------------
Eric Wilson
Director, Integrations and Enablement
Blue Prism Digital Exchange
------------------------------
- « Previous
-
- 1
- 2
- Next »
Related Content
- MS Excel VBO - Exception has been thrown by the target of an invocation in Product Forum
- Stuck: Cannot Open a Blue Prism Object or Process in Product Forum
- Decipher requires "refresh region" to accurately capture characters in Product Forum
- POST API on Blue prism in Product Forum
- VenturIQ-Azure Storage Utility - The input is not a valid Base-64 in Product Forum

