- SS&C Blue Prism Community
- Get Help
- Product Forum
- Credentials Control
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
30-05-22 08:28 PM
Hi!
You can share details of how your robots' credentials are managed?
Do you use any interface or change manually in Blue Prism?
------------------------------
José Francisco Bezerra Nunes Júnior
------------------------------
Answered! Go to Answer.
Helpful Answers
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
31-05-22 01:09 PM
Blue Prism does not gives us any such means of retrieving the credentials from any separate interface or window that I can tell you. Also, it does not have any API or command line code to get the credentials as well. And this I think is due to the nature of what we are asking here. Ideally they can't provide any other ways of retrieving it which can cause compliance issue or violate any governance policies.
But there are some workarounds, first one would be to directly access the backend database of Blue Prism and there is a table called
BPACredentials which will give you Username and Password but the password is stored in an encrypted format so you may not be able to decipher it without the encryption key which Blue Prism uses internally while using get credential action. But, if you store the password as some other parameter value then you could access the value from BPACredentialsProperties Now for making it accessible, you would require to create a front end app and connect it to the backend database it via an API to get the results. But I don't recommend this approach as it can cause performance issue for your database and put a lot of load as well.The second approach can be to create a process which accepts an input parameter say credential name and gives you two output parameters which would be 'Username' and 'Password'. Now, this process can be exposed as a webservice and you can either let the users call the API directly or use this API in some front end application or a chatbot system to make the user interaction possible. I do have a video where I integrated Google Chatbot With Blue Prism that can give you some idea: Google Dialog Flow Chatbot Integration With Blue Prism
However, such a use case is kind of critical and risky in nature so I think that is the reason why you don't have any readymade solution for it but like I mentioned you always can invent the new wheel if situation demands that.
------------------------------
----------------------------------
Hope it helps you out and if my solution resolves your query, then please mark it as the 'Best Answer' so that the others members in the community having similar problem statement can track the answer easily in future
Regards,
Devneet Mohanty
Intelligent Process Automation Consultant | Sr. Consultant - Automation Developer,
WonderBotz India Pvt. Ltd.
Blue Prism Community MVP | Blue Prism 7x Certified Professional
Website: https://devneet.github.io/
Email: devneetmohanty07@gmail.com
----------------------------------
------------------------------
Hope this helps you out and if so, please mark the current thread as the 'Answer', so others can refer to the same for reference in future.
Regards,
Devneet Mohanty,
SS&C Blueprism Community MVP 2024,
Automation Architect,
Wonderbotz India Pvt. Ltd.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
30-05-22 11:56 PM
I am a bit confused from your question in understanding if you are referring to the credentials of any application for the service account of the robot or the windows credential itself which the robot uses to log in to the VDI?
If you mean storing the credential of any application for robots, then yes we use 'Credential Manager' functionality of Blue Prism which is ideally present under your system tab:
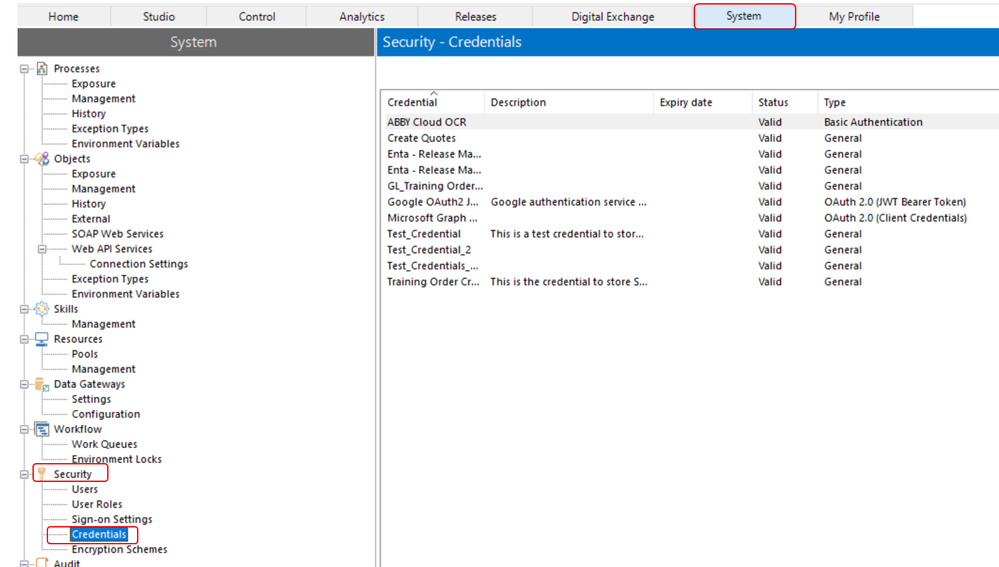
One of the best practices that is followed while storing any credential is that we store the credentials for any application with a credential name that comprises of:
<RESOURCE_MACHINE_NAME>:<APPLICATION_NAME>For example, let us assume I want to store credentials to log into Workday and my resource name is: DESKTOP-C391FA9, then I will be creating one credential item in my Credential Manager with the name as:
DESKTOP-C391FA9:WorkdayWe do this as tomorrow if we scale and let say there are multiple robots which would be using this same workday application then in order to fetch the respective credentials from each robot machine we can use the 'Get' action from 'Internal - Credentials' VBO which helps us to get the parameter stored for a supplied credential name and this credential name that we will pass would be something like:
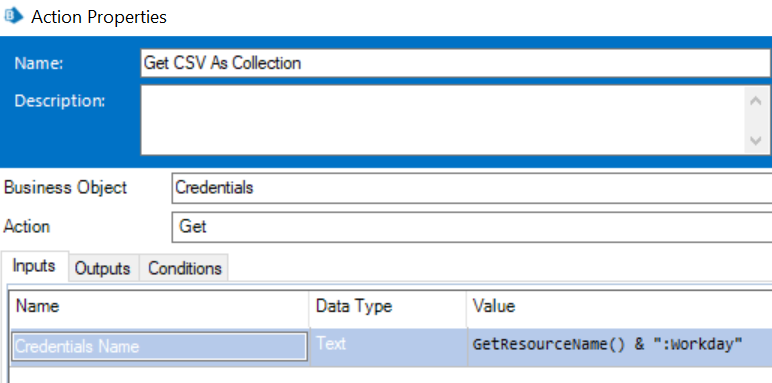
So ideally this function,
GetResourceName() whenever is executed by any bot it will set the machine name of that bot itself and hence the credential name formed as a result of this would ideally map to the credential stored for that bot only. This is how multiple service accounts for each individual bot can be stored while accessing any application credential.Now, if you mean the second part of my understanding which was how we store credentials of any individual bot's service account to login into the Windows OS itself, then that is ideally done with the help of third party credential management and storage tools such as 'CyberArk', 'strongDM', 'Thycotic' and many more software. The benefit of using such systems are first they securely store your credentials and they can be only fetched via some secure mechanism like passing encrypted tokens, also a review approval process can be setup which when approved by someone will only allow the credential to be fetched. Secondly, they have algorithms which can update these passwords automatically after a set interval of time and the same can be incorporated as the login password all via API's. Thirdly, auditing becomes a lot more easier as anyone can track who requested for what credentials at what particular time and if approved who approved the request and so on. I have however, seen one client where they had a master bot in Blue Prism which used to store all these credentials, change the passwords regularly at a set interval of time and manage the accesses of the same using Blue Prism Credential Manager functionality along with some internal API integrations with a SQL server database but well generally I have not seen that kind of practice being followed when it comes to storing the credential of a service account of a robot.
------------------------------
----------------------------------
Hope it helps you out and if my solution resolves your query, then please mark it as the 'Best Answer' so that the others members in the community having similar problem statement can track the answer easily in future
Regards,
Devneet Mohanty
Intelligent Process Automation Consultant | Sr. Consultant - Automation Developer,
WonderBotz India Pvt. Ltd.
Blue Prism Community MVP | Blue Prism 7x Certified Professional
Website: https://devneet.github.io/
Email: devneetmohanty07@gmail.com
----------------------------------
------------------------------
Hope this helps you out and if so, please mark the current thread as the 'Answer', so others can refer to the same for reference in future.
Regards,
Devneet Mohanty,
SS&C Blueprism Community MVP 2024,
Automation Architect,
Wonderbotz India Pvt. Ltd.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
31-05-22 06:49 AM
You can change manually or create automation process to change password and update the credentials in the BP.
------------------------------
Devendra Kumar Prajapati
RPA Manager
Infosys
Chandigarh, India
------------------------------
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
31-05-22 12:12 PM
Hi, @devneetmohanty07 thank you very much for your excellent explanation
I was wondering if there is a more direct way for the key user to change their passwords in an easier way.
Let me give you some context...
We have a lot to manage. Every time once a meeting has expired we must contact the key user of the robot (from the commercial area) and schedule a meeting to change a password. By "direct way" I mean "the key user himself can change his credentials without opening the Blue Prism interface". Is there any interface, web application or something else that can provide this for us?
------------------------------
José Francisco Bezerra Nunes Júnior
------------------------------
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
31-05-22 01:09 PM
Blue Prism does not gives us any such means of retrieving the credentials from any separate interface or window that I can tell you. Also, it does not have any API or command line code to get the credentials as well. And this I think is due to the nature of what we are asking here. Ideally they can't provide any other ways of retrieving it which can cause compliance issue or violate any governance policies.
But there are some workarounds, first one would be to directly access the backend database of Blue Prism and there is a table called
BPACredentials which will give you Username and Password but the password is stored in an encrypted format so you may not be able to decipher it without the encryption key which Blue Prism uses internally while using get credential action. But, if you store the password as some other parameter value then you could access the value from BPACredentialsProperties Now for making it accessible, you would require to create a front end app and connect it to the backend database it via an API to get the results. But I don't recommend this approach as it can cause performance issue for your database and put a lot of load as well.The second approach can be to create a process which accepts an input parameter say credential name and gives you two output parameters which would be 'Username' and 'Password'. Now, this process can be exposed as a webservice and you can either let the users call the API directly or use this API in some front end application or a chatbot system to make the user interaction possible. I do have a video where I integrated Google Chatbot With Blue Prism that can give you some idea: Google Dialog Flow Chatbot Integration With Blue Prism
However, such a use case is kind of critical and risky in nature so I think that is the reason why you don't have any readymade solution for it but like I mentioned you always can invent the new wheel if situation demands that.
------------------------------
----------------------------------
Hope it helps you out and if my solution resolves your query, then please mark it as the 'Best Answer' so that the others members in the community having similar problem statement can track the answer easily in future
Regards,
Devneet Mohanty
Intelligent Process Automation Consultant | Sr. Consultant - Automation Developer,
WonderBotz India Pvt. Ltd.
Blue Prism Community MVP | Blue Prism 7x Certified Professional
Website: https://devneet.github.io/
Email: devneetmohanty07@gmail.com
----------------------------------
------------------------------
Hope this helps you out and if so, please mark the current thread as the 'Answer', so others can refer to the same for reference in future.
Regards,
Devneet Mohanty,
SS&C Blueprism Community MVP 2024,
Automation Architect,
Wonderbotz India Pvt. Ltd.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
31-05-22 02:42 PM
For updating the credentials - What we have done in my past org is a bot was designed till login screen which can change the password in GUI(we were using legacy application with no API etc).
Once password is changed in target application GUI , it is updated back in credential manager via Set credential action and update the new expiry date.
This bot is for all type of cases which have come across in logistics process like Password expired, password not working, User not valid, User locked etc.
------------------------------
Neeraj Kumar
Technical Architect
------------------------------
- Blue Prism - Amazon Textract Authentication with IAM Roles and Not IAM User in Product Forum
- Blue Prism - Amazon Textract Authentication with IAM Roles and Not IAM User in Digital Exchange
- BP HUB Unable to get Refresh after adding New Connection in Product Forum
- Blue Prism 7.3.2 Element Not working in UI in Product Forum
- Process fails to identify web elements when not logged into server in Product Forum

