Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- SS&C Blue Prism Community
- Get Help
- Digital Exchange
- Error When using Send Chat Message action of Micro...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Error When using Send Chat Message action of Microsoft Graph Teams API
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
06-08-22 04:18 PM
Dear Team,
i m trying to send my first Teams Message with the Teams API.
i can generate the access token with the VBO Graph Authentication. but when im about to send a chat message i have the error below.
any ideay to fix it please.?
"Internal : Unexpected error Error during Web API HTTP Request
HTTP Status Code: 412
HTTP Response Content: {"error":{"code":"PreconditionFailed","message":"Requested API is not supported in application-only context","innerError":{"date":"2022-08-06T15:11:04","request-id":"e623181d-9c7f-4a69-8ead-4de0e74c3072","client-request-id":"e623181d-9c7f-4a69-8ead-4de0e74c3072"}}}"
------------------------------
Kouadio ANDOKOU
------------------------------
i m trying to send my first Teams Message with the Teams API.
i can generate the access token with the VBO Graph Authentication. but when im about to send a chat message i have the error below.
any ideay to fix it please.?
"Internal : Unexpected error Error during Web API HTTP Request
HTTP Status Code: 412
HTTP Response Content: {"error":{"code":"PreconditionFailed","message":"Requested API is not supported in application-only context","innerError":{"date":"2022-08-06T15:11:04","request-id":"e623181d-9c7f-4a69-8ead-4de0e74c3072","client-request-id":"e623181d-9c7f-4a69-8ead-4de0e74c3072"}}}"
------------------------------
Kouadio ANDOKOU
------------------------------
7 REPLIES 7
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
08-08-22 03:49 AM
@Kouadio ANDOKOU,
What type of token are you creating? It sounds like you might be generating an Application token. If that is the case, you'll find that much of the Teams API in Graph is not available to you. Graph really wants you to use User tokens which means your digital workers should have their own AD identities.
Cheers,
------------------------------
Eric Wilson
Director, Integrations and Enablement
Blue Prism Digital Exchange
------------------------------
What type of token are you creating? It sounds like you might be generating an Application token. If that is the case, you'll find that much of the Teams API in Graph is not available to you. Graph really wants you to use User tokens which means your digital workers should have their own AD identities.
Cheers,
------------------------------
Eric Wilson
Director, Integrations and Enablement
Blue Prism Digital Exchange
------------------------------
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
15-12-22 04:56 PM
Bumped into the same issue. @Kouadio ANDOKOU, where you able to fix it? I have given the API delegate access (and even application) to send messages on my behalf and while running the VBO in debug mode (no extra AD identity needed since I am running everything on my PC, not on a worker) I still get this error.
Eric Wilson, is there anything I am missing? I already have the token working, and my VBO looks ready to send messages, however I get that error.
Thank you.
------------------------------
Kevin Rodriguez
------------------------------
Eric Wilson, is there anything I am missing? I already have the token working, and my VBO looks ready to send messages, however I get that error.
Thank you.
------------------------------
Kevin Rodriguez
------------------------------
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
15-12-22 05:47 PM
@Kevin Rodriguez,
I'm not sure what you mean by "no extra AD identity needed...". Even if you're running this locally, you have to request a token using the authentication VBO and then pass that token into the Teams Web API. Are you doing that?
Cheers,
------------------------------
Eric Wilson
Director, Integrations and Enablement
Blue Prism Digital Exchange
------------------------------
I'm not sure what you mean by "no extra AD identity needed...". Even if you're running this locally, you have to request a token using the authentication VBO and then pass that token into the Teams Web API. Are you doing that?
Cheers,
------------------------------
Eric Wilson
Director, Integrations and Enablement
Blue Prism Digital Exchange
------------------------------
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
15-12-22 07:58 PM
Thank you for your prompt reply. Yes, sorry, I have authenticated and used the token into Teams Web API and didn't work, I get the same error as the original post. Please find below some screenshots:
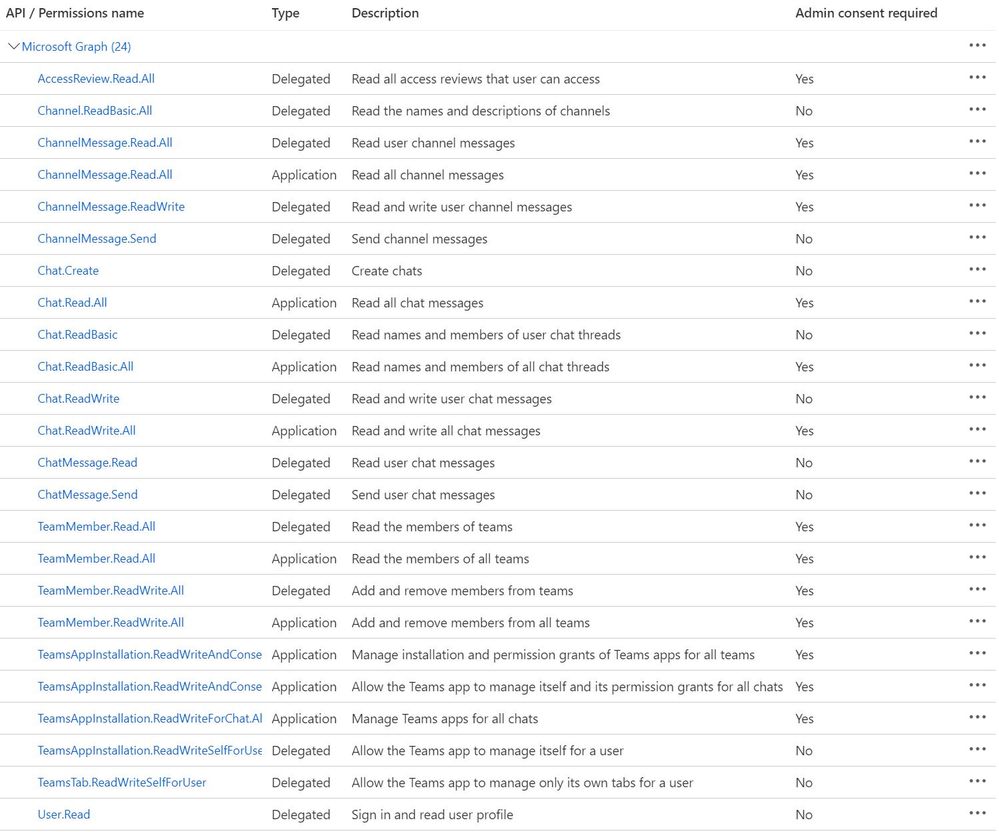
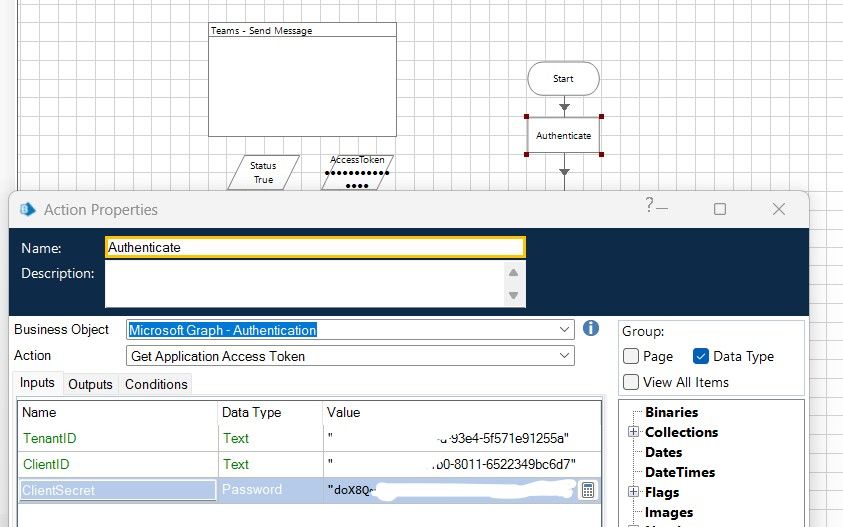
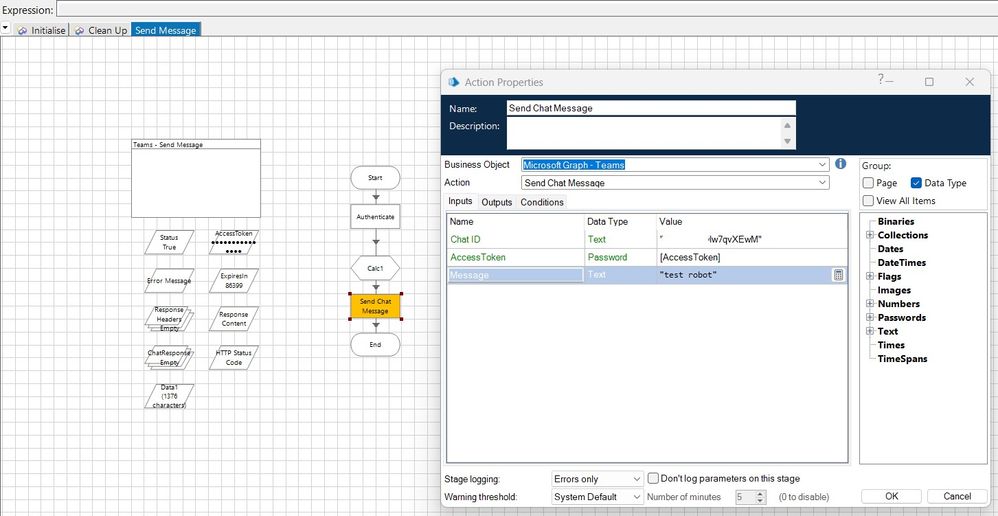 I've set everything under my Azure Portal (client ID, secret, permissions), but I am not sure what else I need to set up in order to send messages through the Teams API.
I've set everything under my Azure Portal (client ID, secret, permissions), but I am not sure what else I need to set up in order to send messages through the Teams API.
Thank you!
------------------------------
Kevin Rodriguez
------------------------------


 I've set everything under my Azure Portal (client ID, secret, permissions), but I am not sure what else I need to set up in order to send messages through the Teams API.
I've set everything under my Azure Portal (client ID, secret, permissions), but I am not sure what else I need to set up in order to send messages through the Teams API. Thank you!
------------------------------
Kevin Rodriguez
------------------------------
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
15-12-22 11:26 PM
@Kevin Rodriguez,
As I mentioned earlier in the thread, the Teams API doesn't expose many actions that can be used with an Application Access token. The majority require that you have a Delegated Access token. Delegated Access tokens require a Client ID, Client Secret, Username, and Password as shown in the example below:
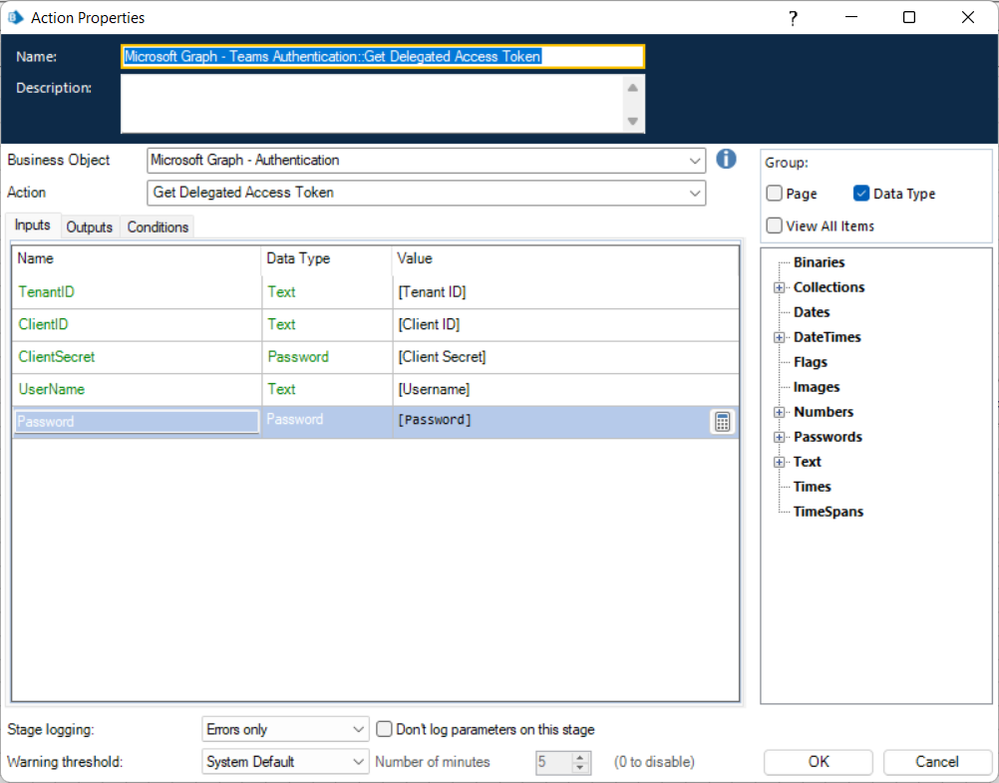
For Username and Password, you could use your own credentials or have a dedicated AD user account created for a digital worker and use that instead.
Cheers,
------------------------------
Eric Wilson
Director, Integrations and Enablement
Blue Prism Digital Exchange
------------------------------
As I mentioned earlier in the thread, the Teams API doesn't expose many actions that can be used with an Application Access token. The majority require that you have a Delegated Access token. Delegated Access tokens require a Client ID, Client Secret, Username, and Password as shown in the example below:

For Username and Password, you could use your own credentials or have a dedicated AD user account created for a digital worker and use that instead.
Cheers,
------------------------------
Eric Wilson
Director, Integrations and Enablement
Blue Prism Digital Exchange
------------------------------
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
16-12-22 03:06 PM
Thank you for your reply, Eric. That makes sense, I should be using Get Delegated Access Token instead. I tried it with my credentials and I get error "The remote server returned an error: (500) Internal Server Error.". I used the user/password that I log in to Azure Portal, where previous screenshots were taken. I also created another secret, but it didn't matter if the credentials are correct, I get a 500 error. Please see below my configuration:
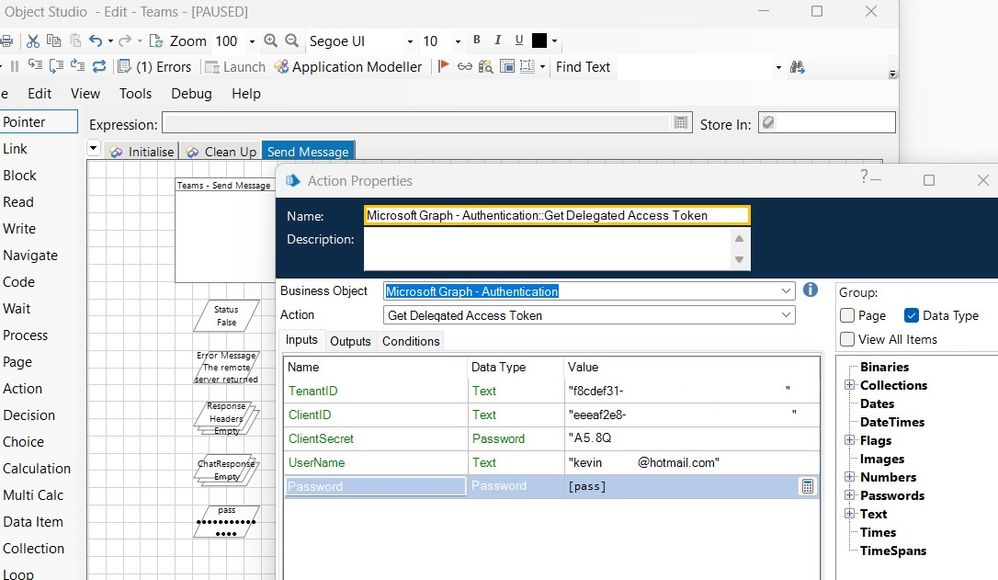
Is there anything I should be doing beforehand? I can say connection works, as using Get Application Access Token still works and generates a token.
Quick overview:

Thank you so much for all your support!
------------------------------
Kevin Rodriguez
------------------------------

Is there anything I should be doing beforehand? I can say connection works, as using Get Application Access Token still works and generates a token.
Quick overview:

Thank you so much for all your support!
------------------------------
Kevin Rodriguez
------------------------------
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
16-12-22 03:21 PM
@Kevin Rodriguez,
It's been a while since I set up my test environment, but as I recall there's a "trick" to delegated access. The idea behind delegated access is that when an application attempts to work on behalf of another user the user should be presented with the pop-up browser window, notified of the request, and given the option to accept or reject the delegation. In this case, we're not presenting a window for this as this is functionality that's generally run un-attended. Luckily, Microsoft considered this.
When you assign the permissions to the client ID/client secret credential you created in Azure, there's an option to grant admin consent upfront. Just click the button/link referenced below and it will automatically provide the overall consent for the credential. I think that will take care of it for your use of a delegated access token.
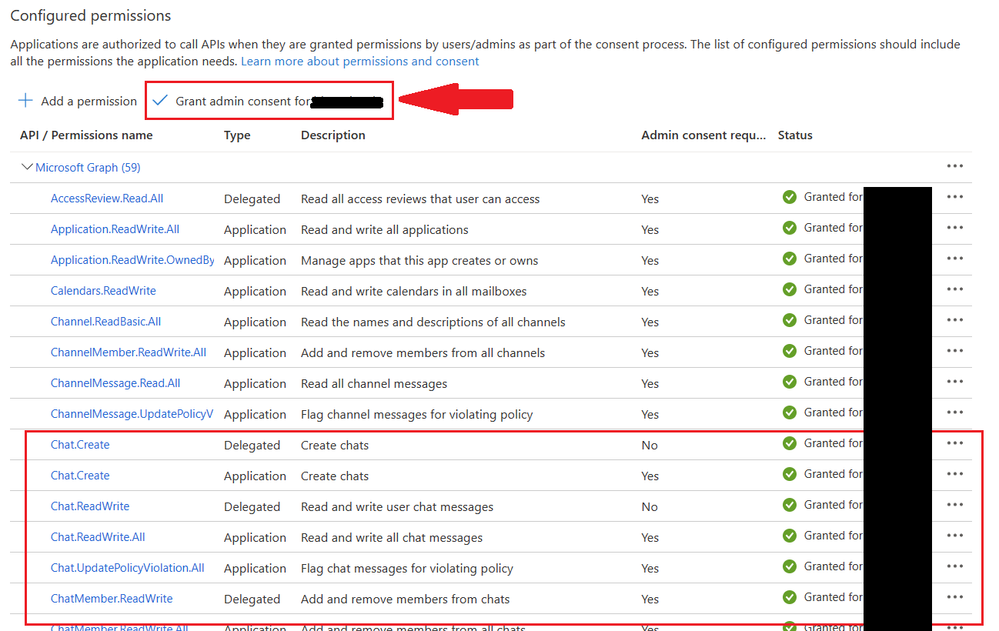
Cheers,
------------------------------
Eric Wilson
Director, Integrations and Enablement
Blue Prism Digital Exchange
------------------------------
It's been a while since I set up my test environment, but as I recall there's a "trick" to delegated access. The idea behind delegated access is that when an application attempts to work on behalf of another user the user should be presented with the pop-up browser window, notified of the request, and given the option to accept or reject the delegation. In this case, we're not presenting a window for this as this is functionality that's generally run un-attended. Luckily, Microsoft considered this.
When you assign the permissions to the client ID/client secret credential you created in Azure, there's an option to grant admin consent upfront. Just click the button/link referenced below and it will automatically provide the overall consent for the credential. I think that will take care of it for your use of a delegated access token.

Cheers,
------------------------------
Eric Wilson
Director, Integrations and Enablement
Blue Prism Digital Exchange
------------------------------
Related Content
- MS - Excel VBO Find or Go to Cell action action not working in Product Forum
- How to integrate Microsoft team with Blue prism 6.10 version in Product Forum
- BPE - BP UI automation - Roles assigned - Tree view error in Product Forum
- Error when Invoking JavaScript in Product Forum
- HUB upgrade fails on installing Gateway in Product Forum

