- SS&C Blue Prism Community
- Get Help
- Digital Exchange
- New Connector for Microsoft Office 365 - Outlook R...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
New Connector for Microsoft Office 365 - Outlook Released!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
03-10-22 01:46 PM
A new connector is available, on the Digital Exchange, for working with Microsoft Office 365 - Outlook. This is a complete design of the previous Microsoft Graph API - Outlook connector.
The new connector is implemented as a traditional VBO (Visual Business Object), so there are no issues with being able to download and save attachments directly from the connector. This connector has similar actions to the legacy Outlook VBO, but since it leverages Microsoft Graph API, behind the scenes, it does not require Outlook to be installed locally on the runtime resource.
Some things to be aware of:
- The legacy Outlook VBO exposed multiple actions (i.e. Basic, Advanced, and Expert) for retrieving emails from the Inbox or Sent Items folders. The new VBO simplifies and consolidates these multiple actions into a single action that support OData $search and $filter options. Refer to the documentation for links to further Microsoft information about using these properties.
- Microsoft limits the size of attachments when sending emails via the Graph API. Their documentation is a little confusing on what the actual max size is. The Graph API documentation implies that singular file attachments can be up to 150MB each, but Exchange Online limits the overall size of a Message (i.e. headers, body, attachments, etc all together) to no more that 150MB. In our testing, the latter appears to be the actual case.
You can find the new connector at the following link:
Microsoft Office 365 - Outlook
#BPTechTips #DigitalExchange #Outlook
Cheers,
------------------------------
Eric Wilson
Director, Integrations and Enablement
Blue Prism Digital Exchange
------------------------------
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
30-01-23 02:56 PM
hi,
just out of interest - are you guys planning to update this to a version that takes Tennant/Client ID/Client Secret as input in future?
With the current version these variables are hardcoded within the object, so:
a) not very secure
b) downloading new version from DX and installing it overrides these details
c) if you're using separate T/CID/CS for Dev and Prod you need to modify the object in PROD after release.
none of above strikes me as desirable/best practice.
Additionally, currently within Microsoft 365 - Outlook the token is not persistent - so calling each function requires additional API call to re-authenticate- which ultimately doubles the amount of traffic/API calls. Would it not make sense to return it to the process level (together with 'timeout' variable) and manage it there (only obtain a new Token if it's expired) - in line with (now depreciated) the previous version of Graph API (using WebAPIs (Microsoft Graph API - Outlook [DEPRECATED]).
Regards
------------------------------
Dawid Pekala
IPA Lead
Lowell Group
Europe/London
------------------------------
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
30-01-23 04:38 PM
I don't think you understand how this VBO works. Tenant/Client ID/Client Secret are accepted as input to the Authenticate action. They are not hardcoded. Refer to the screenshots below. Further, we are not calling the authentication action as part of every other action. We check a global Flag parameter named Authenticated on each action. As long as that flag is True, there's no need to go through the authentication process. If that flag is False, then the Authenticate action is called internally.
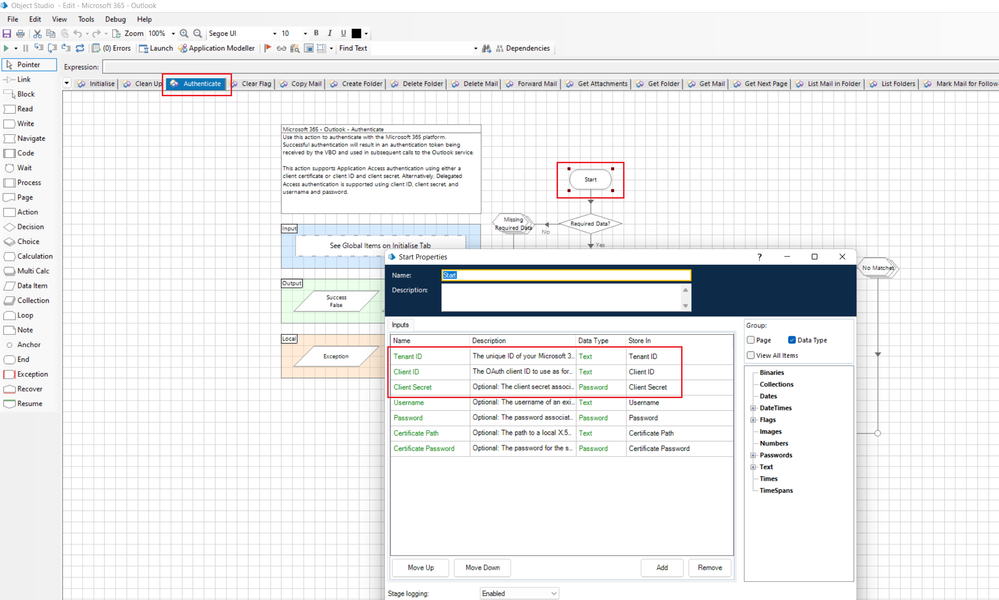
Further, the Access Token, from a successful authentication, is persisted in a global variable named AccessToken which can be found on the Initialise tab.
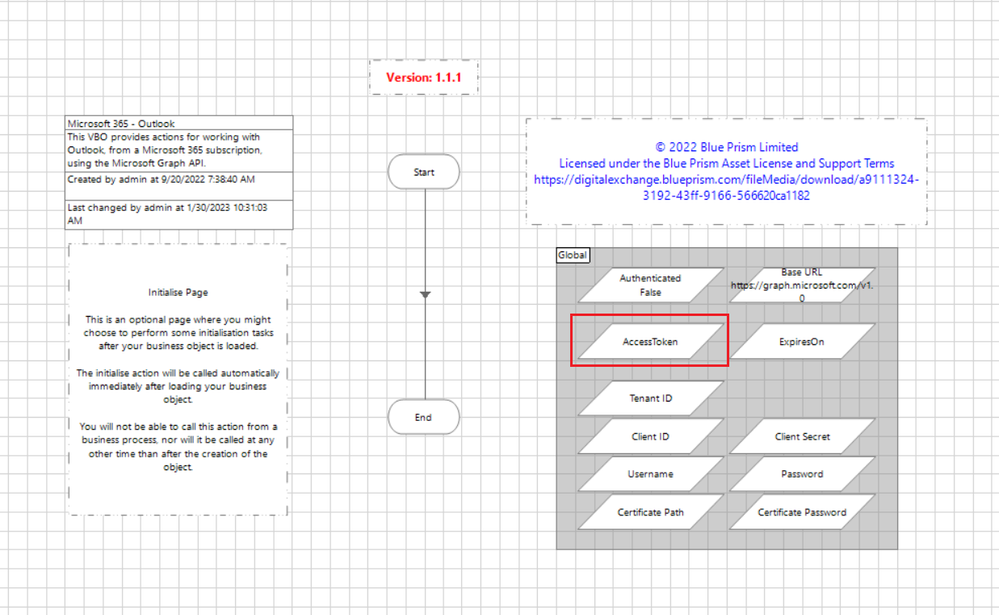
Are you sure you're using the latest version of the VBO available from the DX and that no one in your organization has perhaps customized it or inadvertently saved their local changes?
Cheers,
------------------------------
Eric Wilson
Director, Integrations and Enablement
Blue Prism Digital Exchange
------------------------------
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
30-01-23 05:24 PM
Having a quick look into our DEV, it does seem the object has been somewhat altered and set-up incorrectly to start with.
I'll have a look and see if we can revert it back to the way it supposed to work.
Regards
Dawid Pekala
------------------------------
Dawid Pekala
IPA Lead
Lowell Group
Europe/London
------------------------------
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
21-02-23 03:09 PM
hello @ewilson - I am using the latest VBO and guide to use the new VBO. downloaded the MSAL.net zip file and placed the Dll in the required path.
Passed Client ID, Client Secret, Tenant ID but while Authentication, Getting the error like one or more error is there.
------------------------------
Neeraj Kumar
Technical Architect
------------------------------
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
22-02-23 09:34 PM
We pushed an update to the Microsoft 365 - Outlook VBO this morning. There's a fix for a bug we identified in the Authenticate action when trying to perform a client certificate or username/password authentication. I don't suppose you were attempting either of those?
Cheers,
------------------------------
Eric Wilson
Director, Integrations and Enablement
Blue Prism Digital Exchange
------------------------------
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
23-02-23 09:31 AM
hello Eric Wilson - We are authentication via tenant ID, Client ID, secret ID . details and it is working now fine from 1.1.0 and 1.2.0.
now we are on 1.2.0 version and list mail in folder and sent item are giving 403 forbidden error. we are reviewing the permission configured on Azure.
Can You point out in the mean time what else to check
Mails action are performed on Shared mailbox.
------------------------------
Neeraj Kumar
Technical Architect
------------------------------
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
23-02-23 01:18 PM
I'm having this same issue with the 403 forbidden error - would love any feedback on resolution for this!
------------------------------
Rachel Abbott
------------------------------
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
23-02-23 04:45 PM
Ok, so you're getting an Application Access token and trying to retrieve email from a shared mailbox. Have you verified that the Client ID you have has the proper mail permissions in Azure AD? For shared mailboxes this would include either Mail.Read.Shared or Mail.ReadWrite.Shared for reading from the shared mailbox. You would also need Mail.Send.Shared if you intend to send email from the shared mailbox.
Here's a link to the Microsoft Graph permissions reference:
https://learn.microsoft.com/en-us/graph/permissions-reference#mail-permissions
Cheers,
------------------------------
Eric Wilson
Director, Integrations and Enablement
Blue Prism Digital Exchange
------------------------------
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
23-02-23 04:55 PM
hello Eric Wilson - Yes I have checked the permission w.r.t shared mailbox and it is provided correctly.
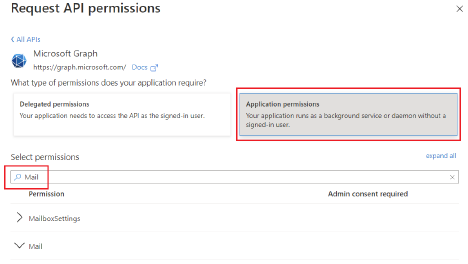
There is one thing which are doing differently on what is mentioned in VBO guide. we are using delegated permission option instead of application permission option.
Can it cause my issue?
------------------------------
Neeraj Kumar
Technical Architect
------------------------------
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
23-02-23 08:58 PM
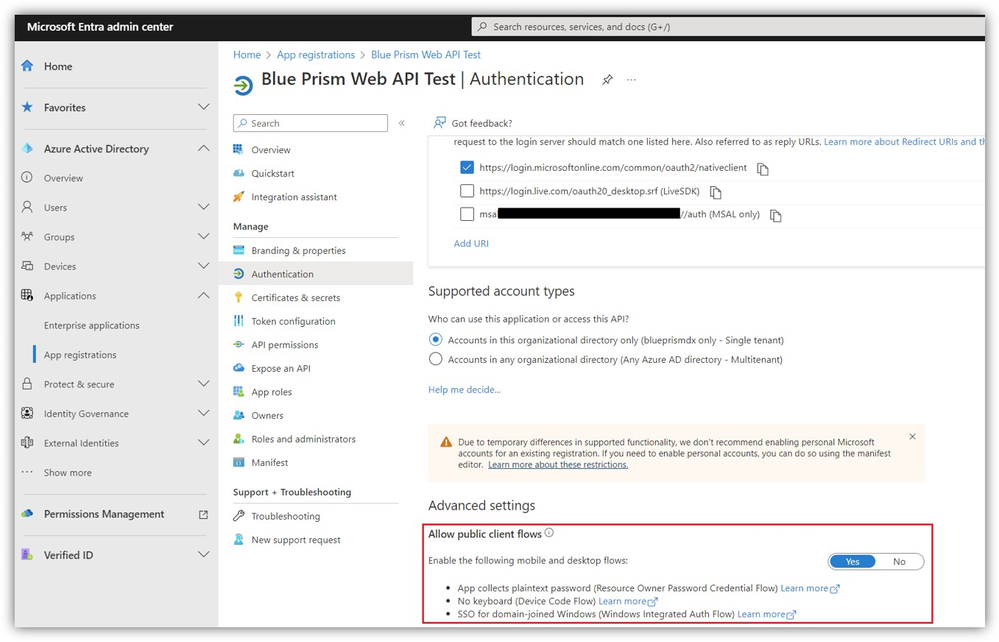
If you're trying to get a Delegated Access token you must pass in the Tenant ID, Client ID, Username, and Password. Do not pass in Client Secret because that automatically results in trying to get an Application Access token. The Username and Password are for the account your Digital Worker is trying to work on-behalf of. Also, I believe Delegated Access will require that you enable the Allow public client flows option within the Application Registration page for the Client ID you're using.
------------------------------
Eric Wilson
Director, Integrations and Enablement
Blue Prism Digital Exchange
------------------------------
- Microsoft 365 - Outlook v1.6.0 Released in Digital Exchange
- Microsoft Dataverse VBO Connectivity Issue in Digital Exchange
- Support for Microsoft Information Protection Labels (aka Sensitivity Labels) in Outlook VBO. in Digital Exchange
- [NOTIFICATION] Issue with Browser automation after Microsoft Edge v128 update in Product Forum
- Attaching files to an list item in SharePoint using API in Product Forum