- SS&C Blue Prism Community
- Get Help
- Product Forum
- Microsoft Graph API setup with Delegated Permissio...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Microsoft Graph API setup with Delegated Permissions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
28-12-22 01:53 PM
Hi all,
We're currently trying to implement Microsoft Graph API to use in our workflows, however we can't seem to work out what exactly we're doing wrong.
Due to security reasons, we're not allowed to grant Blue Prism (V6.6) the Application Permission required to perform certain actions, so using Delegated Permission is the only way to go.
Things to consider for our use case:
- We work in a Citrix environment using VM's;
- For audit reasons, each process has its own robot user account which we use to log into the VM's via SSO;
- All robot user accounts (30+) have been exempt from MFA/2FA, so this shouldn't be an issue;
We've followed the documentation and set all prerequisites:
- Created an App Registration in our Azure AD;
- Set the API permissions (Files.ReadWrite.All and Sites.ReadWrite.All);
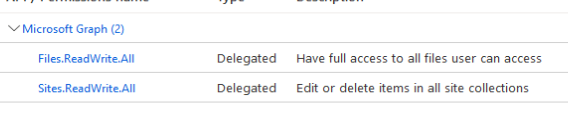
When using the action "Get Delegated Access Token" with mandatory parameters, we are unable to get a successful response back:
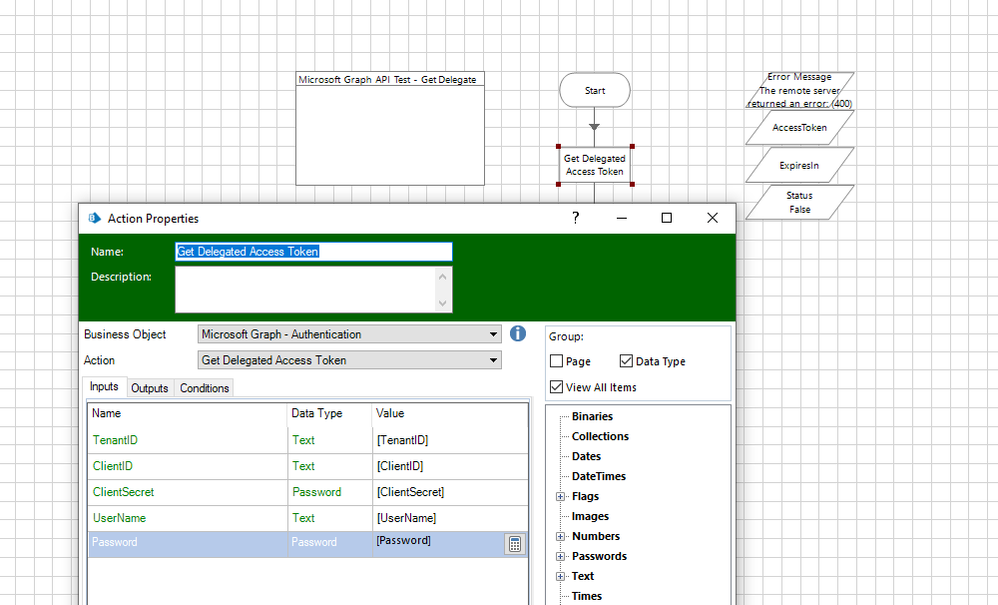
The only response we get is either a bad response ("The remote server returned an error: (400) Bad Request." or "(401) Unauthorized").
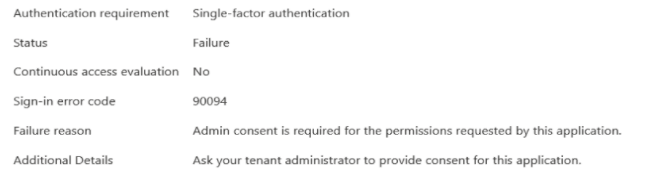
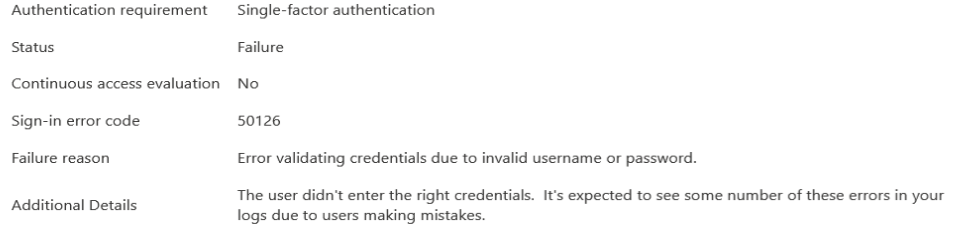
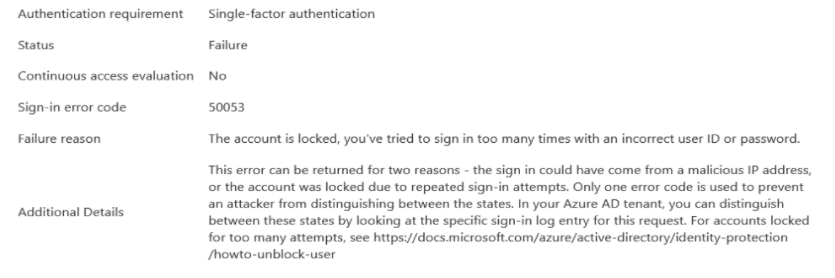
In the AD logs, we get a few more detailed exception details, but they don't really help us figuring out what the issue is. Without changing the credentials, we get a mix of errors varying from "admin consent required", "invalid credentials" and "account locked"... We're sure every parameter contains the right value (username/password/tenant_id/client_id/client_secret are valid).
I guess my question is, are we missing something in our setup? Or is the "Admin consent required" part the key issue here?
The funny thing is, when using the action "Get Application Access Token", we are able to retrieve a token, even though we have not given BP Application Permissions. So I'm guessing this is a token without any permissions? Because said token didn't allow us to use other API's (such as SharePoint), when we tested it just to be sure.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
03-01-23 10:04 AM
The answer for your first question is I had meetings with Azure teams and security teams within the company trying to understand why that was failing. Specially as it was working fine on Postman so it couldn't be a call or Microsoft issue. Additionally, the Authentication VBO was already in use by a lot of people and they are happy with it, which also means it couldn't be a VBO problem. That only left the possibility of having the issue on the company level. Having a meeting with those teams to track the requests and how they are being handled provided the conclusion.
Regarding your second question, you are correct. Microsoft Graph - Authentication VBO is no longer need. Both of them will give you access token and you need only one of them.
Regarding using the access token in the sharepoint VBO, I can't comment on that as we do not use this VBO. However, based on the screenshot you provided, it seems that the request body and authentication method as well as the end point will need to be modified. I would suggest you use the WebService for sharepoint graph you can find it in BP Digital Exchange following this link, Connector for Microsoft Graph API - Sharepoint - 2.2.0
You can just pass the token you get through MSAL to the actions in this webservice and it should work.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
03-01-23 04:00 PM
It seems we are indeed facing the same issues regarding security. We tried getting an access token via Postman using grant type 'Authorization Code', and were able to retrieve a token via the authentication route (approving SSO via the authenticator app), however when trying grant type 'Password Credentials' (thus mimicking what the MS Graph Authentication VBO does), it failed just like in BP.
We're going to try your route with the MSAL.NET library and hopefully see the same results as you. I'll mark your answer as the best answer/solution if this works. Thank you for your help so far!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
03-01-23 04:11 PM
Carla - The MSAL.NET VBO is definitely the preferred authentication VBO for Microsoft Graph. Our plans are to deprecate the Microsoft Graph - Authentication VBO. The MSAL.NET VBO provides support for more authentication types including: Client ID, Certificate, Integrated Windows, and Username/Password.
Cheers,
Eric
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
24-01-24 04:22 PM
Hi @ewilson, I am getting below error while trying to authenticate delegated access using action Get Delegated Access Token in Blue Prism. Any suggestions?
{"error":"invalid_grant","error_description":"AADSTS50034: The user account ***** does not exist in the 07bef031-67e8-4f56-a63c-10a9f0466774 directory. To sign into this application, the account must be added to the directory. Trace ID: f46e2ac3-0d81-4b75-a060-99ad72c76d00 Correlation ID: f892eba9-fa5d-4dcb-b7c4-cc0e05e9e78f Timestamp: 2024-01-23 13:58:35Z","error_codes":[50034],"timestamp":"2024-01-23 13:58:35Z","trace_id":"f46e2ac3-0d81-4b75-a060-99ad72c76d00","correlation_id":"f892eba9-fa5d-4dcb-b7c4-cc0e05e9e78f","error_uri":"https://login.microsoftonline.com/error?code=50034"}
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
24-01-24 06:24 PM
Hello @vinod ch,
It would be best to create a new thread for your question, but in the meantime it appears you either have the wrong tenant ID or the wrong user ID. In either case, the user ID you're referencing doesn't exist within the Azure AD of the tenant you've specified. You need to verify both ID's.
Cheers,
Eric
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
26-01-24 01:25 PM
Hi @ewilson
As suggested, Created separate Thread - https://community.blueprism.com/discussion/graph-api-delegated-access
And FYI I am using Correct User ID and Tenant ID and User ID is also existed within Azure AD because I am using same Tenant ID and User ID in Power Automate where its working and Its failing in Blue Prism and Postman. Can you please suggest on above NEW thread?
Also let me know, How can we verify whether User ID is under mentioned azure AD Tenant or not?
- « Previous
-
- 1
- 2
- Next »
- Can read and copy but not write with Microsoft 365 - Excel in Product Forum
- Securing your Decipher installation in Product Forum
- MFA error while using Microsoft Graph Authentication VBO in Digital Exchange
- Error while getting the access token using microsoft365- outlook(Graph API) in Digital Exchange
- App Service Access Management for SharePoint CRUD - MS Graph API in Product Forum